About Us
Secure Micro Technologies assists the defense industrial base with advanced secure systems prototyping efforts. It offers a full range of solutions for secure, trusted and privacy-preserving services computing systems and applications including advanced cryptographic solutions, digital auditing, logging, and forensics, secure data storage and legacy systems retrofitting, among others.

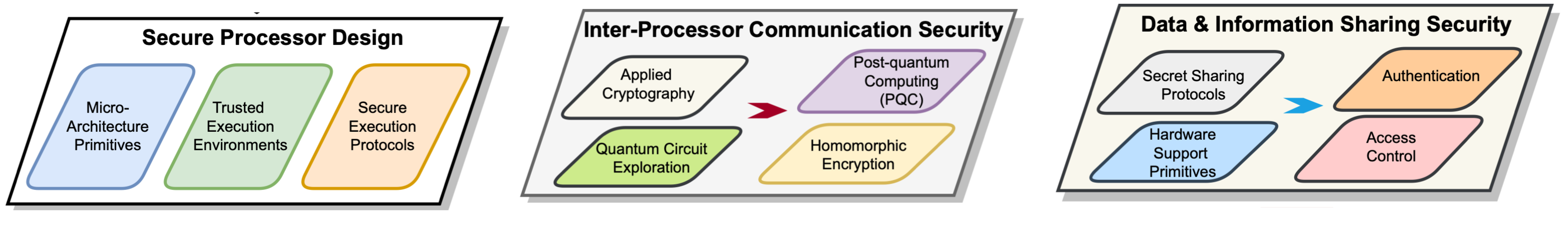
The Secure, Trusted, and Assured Microelectronics (STAM) Center is a research, development, and education unit focusing on establishing the foundation for future secure and trusted semiconductor/microelectronics technologies: (1) new substrates, synthesis, and fabrication, (2) new computing paradigms and architectures, and (3) integrated sensing, edge computing, and secure communications. The center couples its research mission with the active recruiting and training of students targeting applications of national security importance.
Contact
- Advanced crypto-agility
- Customized solutions including low-power and higher efficiency designs
- Application domain-specific acceleration solutions
- Security analysis including side-channel resiliency evaluation, hardware and system penetration testing, etc.
- Transition or migration to post-quantum cryptography
- Quantum-resistant assessment
You can also directly email us at stamcenter _at_ asu _dot_ edu.